CVE-2025-4609: Serious Vulnerability Discovered in Google Chrome
Think of this like a locked backdoor in your home that a thief has discovered; if left unsecured, it can lead to unauthorized access to your personal space. In the case of Google Chrome, this vulnerability, known as CVE-2025-4609, could allow a remote attacker to exploit your browser by sending a specially crafted file, thus potentially bypassing its security layers.
Who is at Risk?
This issue specifically affects Windows users of Google Chrome versions prior to 136.0.7103.113. If you are using an outdated version of Chrome, you might be vulnerable to the following risks:
- Unauthorized access: An attacker might manage to manipulate your browser settings or data.
- Data breaches: Sensitive information stored in your browser could be compromised.
- Disruption of services: Your browser’s functionality may be affected, leading to erratic behavior or crashes.
In simple terms, if your version of Chrome hasn’t been updated, you could be leaving the door open for cyber mischief.
How to Stay Safe
To protect yourself from potential exploitation, it’s crucial to take action immediately. Here’s what you should do:
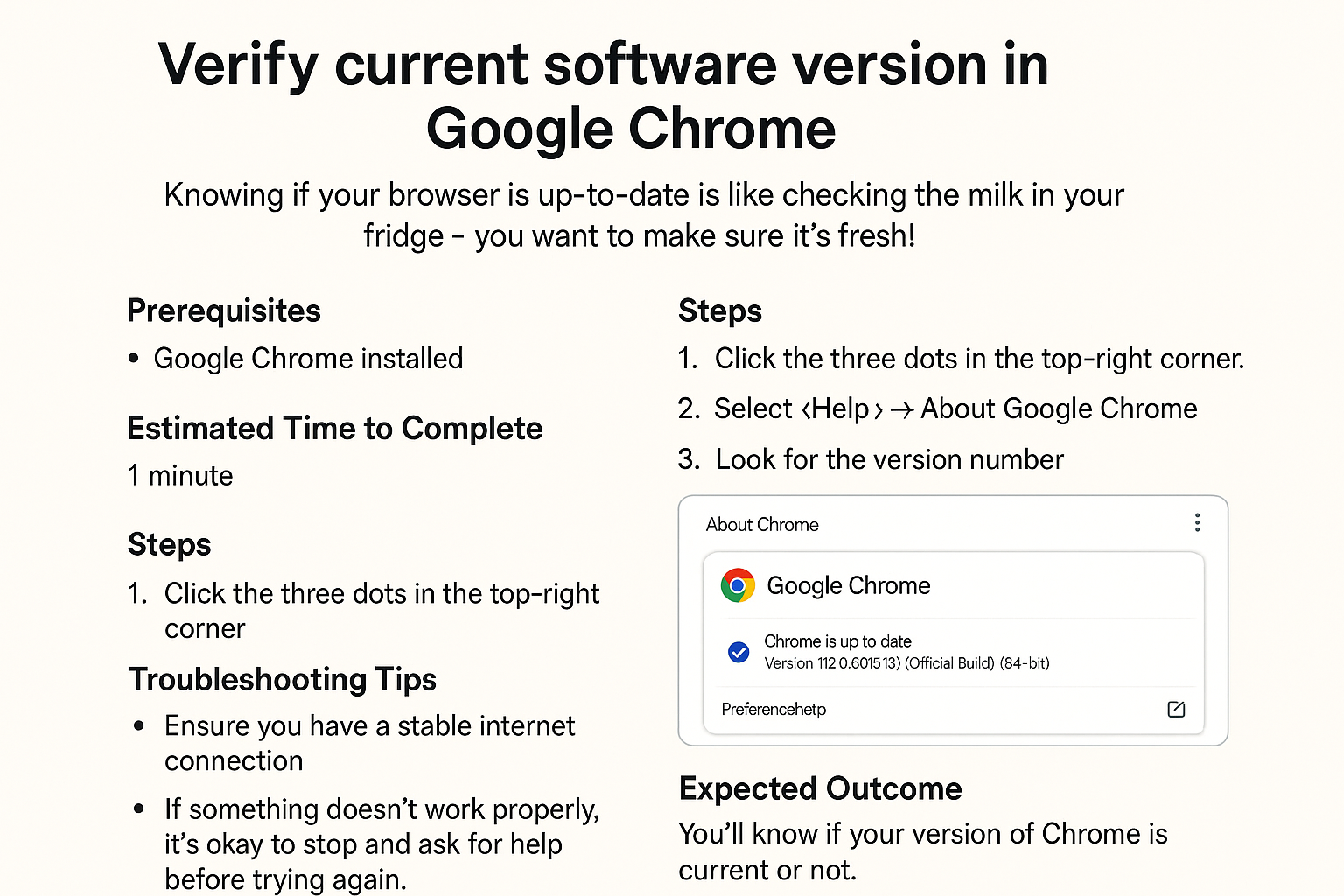
- Update your Chrome browser: Check for updates by clicking the three dots in the upper right corner of Chrome, then navigate to Help > About Google Chrome. This will prompt an automatic update, if needed.
- Monitor for strange behavior: Keep an eye out for any unusual pop-ups or changes in your browser settings after opening files from unknown sources.
- Regularly check your version: Ensure you're running the latest version of Chrome to minimize vulnerabilities in the future.
By updating promptly, you can secure your browsing experience and help prevent a potential breach.
📖 Learn more: Google Chrome Security Updates and CVE Issue Tracking.