Configure Automatic Incident Response Workflows
Just like the smoke alarm protects you from unexpected fires, configuring automatic incident response workflows can help safeguard your information from cyber threats. This guide will walk you through the steps to set up these workflows, making your digital environment safer without needing advanced technical skills. Let’s get started!
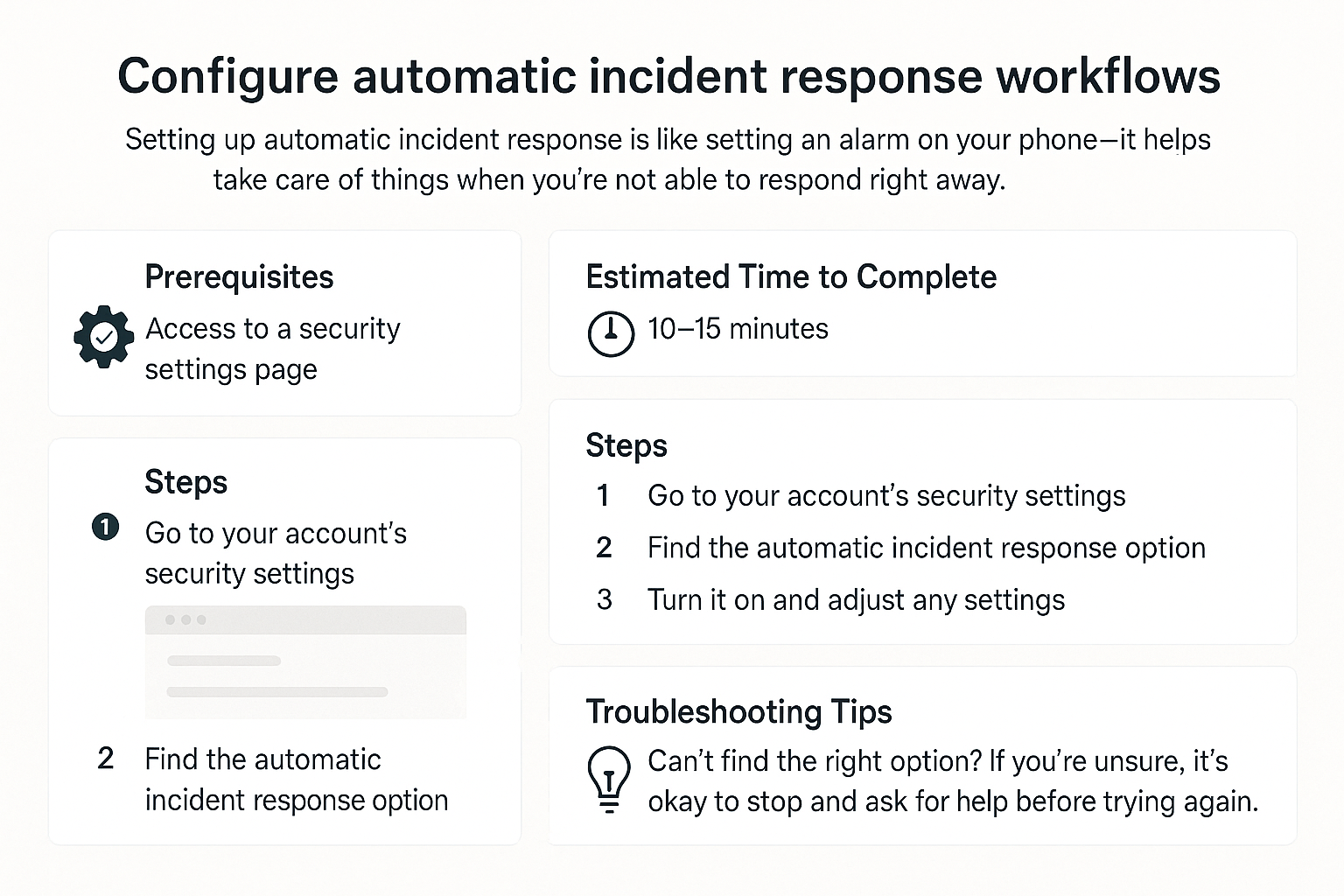
Prerequisites
Before you begin, you'll need to have the following:
- A computer or device with internet access.
- Administrative access to the systems or accounts you want to configure (for example, your email or security platform).
- A basic understanding of your organization's security needs.
Estimated Time to Complete
This task should take approximately 30-45 minutes to complete, depending on your familiarity with the tools you are using.
Steps
-
Identify Your Incident Types
Determine the types of incidents you want to respond to automatically (e.g., phishing emails, malware alerts). Document these incidents. -
Select Your Tools
Choose the security tools or platforms that will support your incident response. Look for ones that offer automation features. Examples include security information and event management (SIEM) tools or endpoint detection and response (EDR) solutions. -
Access the Configuration Settings
Log into the platform you selected and navigate to the settings or configuration section. This is usually found in the dashboard or on a menu. -
Set Up Automation Rules
Create rules for each incident type you identified earlier. For example, if a phishing email is detected, you might want the system to block it and notify the team. Most platforms allow you to fill out forms to specify these actions. -
Test Your Workflows
Once the automations are set, it's crucial to test them to make sure they work. Simulate an incident (like sending a test phishing email) and see if the automated response triggers as expected. -
Monitor and Adjust
After your workflows are live, keep an eye on their performance. You might need to tweak the rules or add new incident types as you learn more about your security landscape.
Troubleshooting Tips
- If You Can't Find the Settings Menu: Make sure you are logged in as an administrator. If you're still having trouble, check the documentation for your specific tool or platform.
- If Your Automation Doesn’t Trigger: Revisit the rules you set up and ensure that they are correctly configured. Sometimes, the actions may depend on specific conditions being met.
- If You're Unsure About Test Incidents: Always do this in a controlled environment or with a colleague present, just to ensure that you're not disrupting work.
If you’re unsure, it’s okay to stop and ask for help before trying again.
Expected Outcome
By following these steps, you should have successfully set up automatic incident response workflows that can help your organization react swiftly to security threats. This proactive approach reduces response time and enhances your overall cybersecurity posture, making you feel more secure in your digital activities.
As you work with these tools, remember: a strong password is your first line of defense. Use at least 12 characters with a mix of letters, numbers, and symbols. Avoid names or birthdays.