CVE-2025-47967: Security Flaw in Microsoft Edge for Android Poses Spoofing Risks
Recently, a vulnerability was discovered in Microsoft Edge for Android that may leave users at risk. Understanding such issues is essential to ensure your online safety.
Who is at Risk and What Could Happen?
This vulnerability affects users of Microsoft Edge on Android devices. When using the browser, such users may unknowingly allow an unauthorized attacker to perform actions that could mislead them. Here are the key points:
- Everyday users of Edge on Android: If you regularly browse the internet using this app, you could be affected.
- Unauthorized attackers: Malicious individuals could exploit this flaw to trick users into believing they are interacting with a legitimate website.
- Lack of clear warnings: Users might not see alarms when engaging in sensitive online activities (like logging in to accounts) due to insufficient warning messages from the app.
Imagine a stranger sneaking a note into a message board that looks official but actually leads you to a fake site. That’s what this vulnerability allows — a way for attackers to disguise their actions.
How to Stay Safe
Acting quickly is crucial. Here are some straightforward steps to protect yourself:
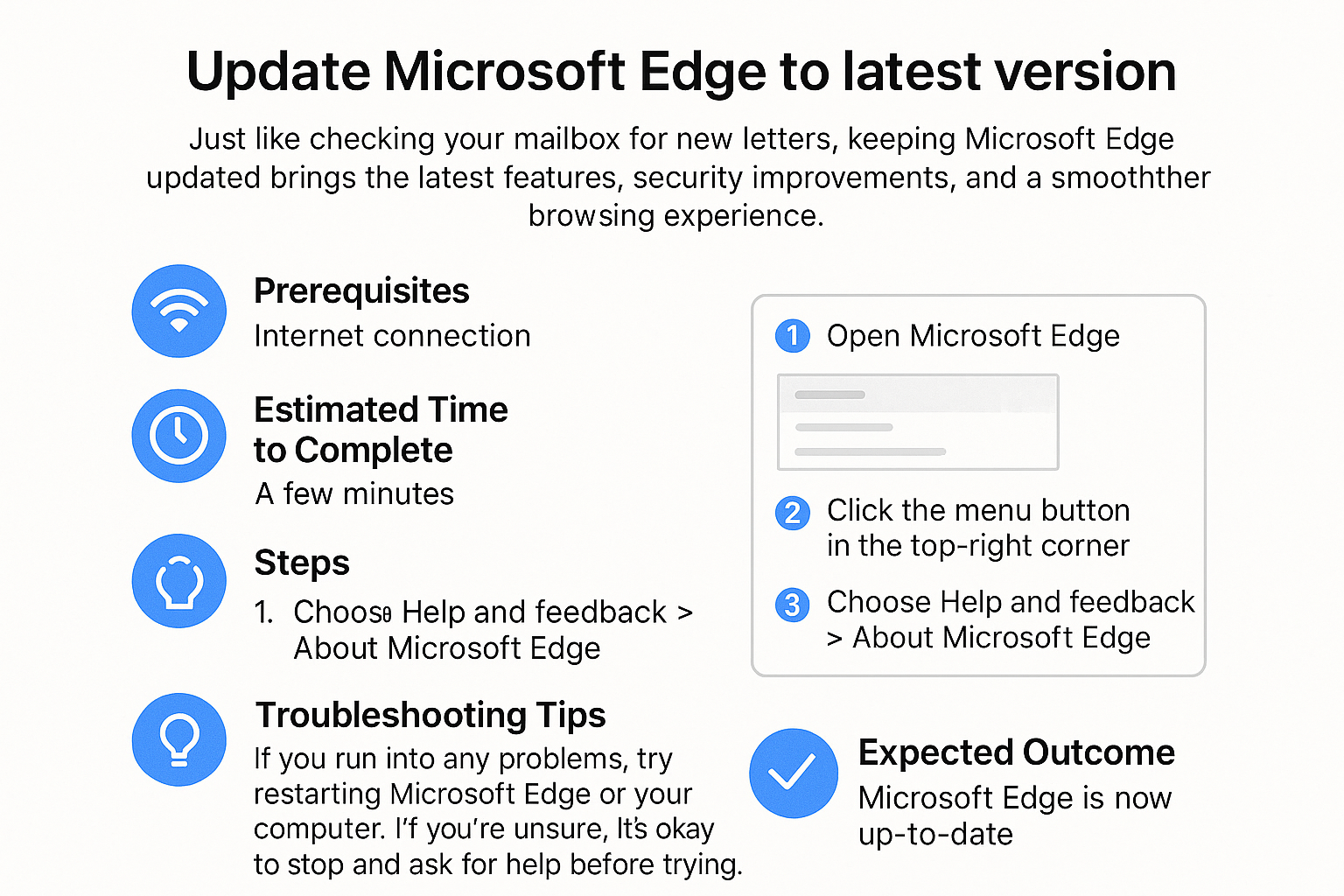
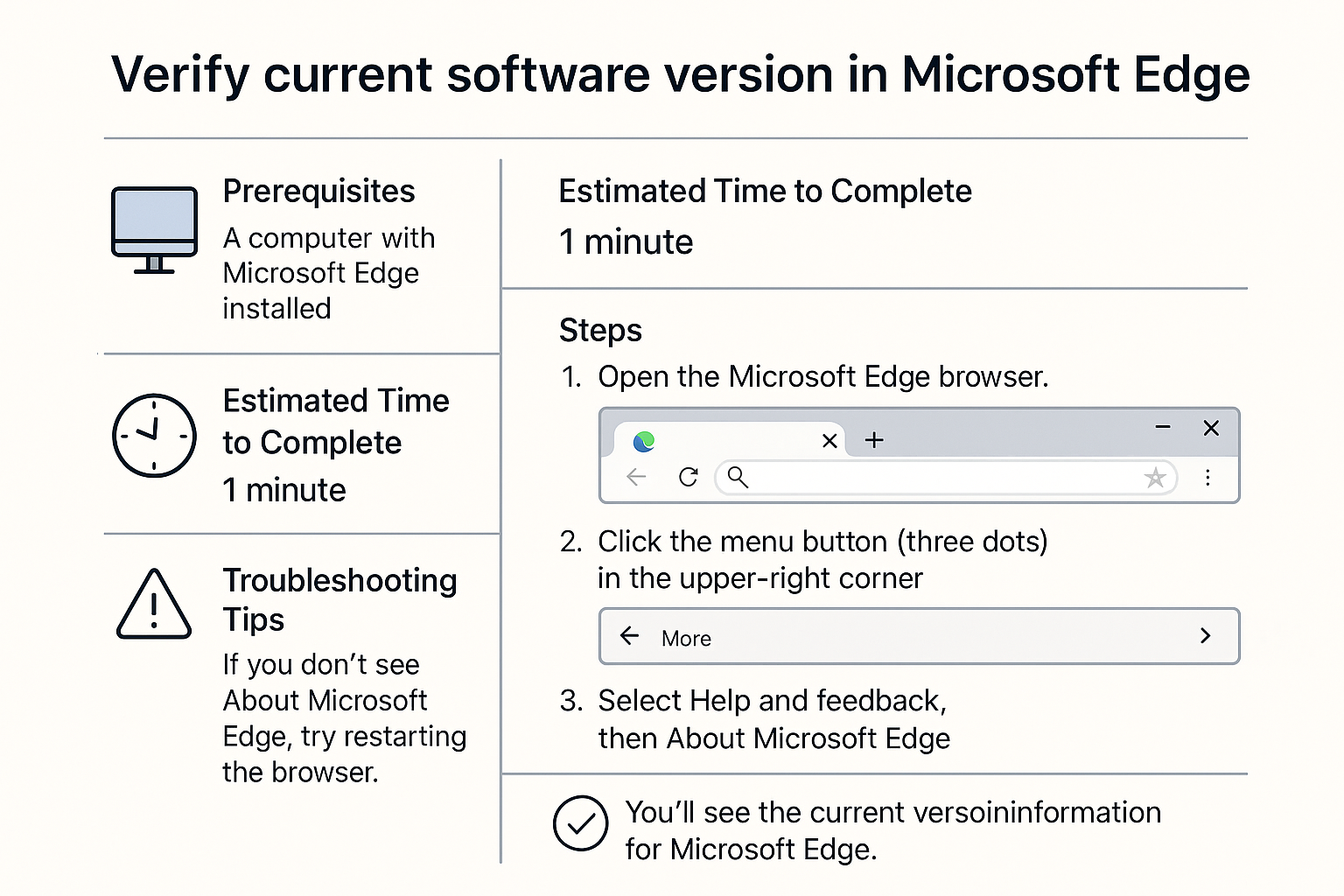
- Update Microsoft Edge: Check for updates by visiting the Google Play Store. Keeping your app up to date patches potential security vulnerabilities.
- Look for security notifications: Pay attention to any warning signs or alerts when browsing — they can be crucial for your online safety.
- Monitor your online accounts: Keep an eye on your accounts for any unusual activity, and report anything suspicious right away.
Taking these actions not only helps protect you but also prevents someone else from exploiting users through this flaw.
📖 Learn more about the security issue here.